Table of Contents
As a substitute for Cobalt Strike, nation-state threat actors are increasingly embracing and incorporating the Sliver command-and-control framework in their infiltration campaigns.
The prominence of Cobalt Strike as an attack weapon has led to advancements in Cobalt Strike defenses, according to Microsoft security specialists. Therefore, “Sliver delivers a compelling alternative for actors seeking a lesser-known toolkit with a low entrance hurdle.”
What is sliver command-and-control framework?
Sliver command-and-control framework is a Go-based open-source C2 platform that allows user-developed extensions, unique implant creation, and various commandeering options. It was first made public by cybersecurity firm BishopFox in late 2019.
A client application that enables the Sliver command-and-control framework operators to communicate with the implants and provide malicious commands is typically included in a C2 framework, according to Microsoft. The server typically accepts connections from implants on a compromised system.
The cross-platform kit is known to provide stagers, which are payloads primarily meant to extract and launch a fully functional backdoor on compromised computers, in addition to providing long-term access to infected hosts.
One of its users is a well-known ransomware-as-a-service (RaaS) affiliate identified as DEV-0237 (also known as FIN12), which has used initial access obtained from other organizations (also known as initial access brokers) in the past to spread ransomware strains like Ryuk, Conti, Hive, and BlackCat.

Sliver command-and-control framework and other post-exploitation tools were recently seen being dropped by cybercriminals via being embedded in the Bumblebee (also known as COLDTRAIN) loader, which replaced BazarLoader earlier this year and has connections to the wider Conti syndicate.
The switch from Cobalt Strike to a freely available tool is interpreted as an effort on the side of adversaries to lessen the likelihood that they will be discovered in a vulnerable setting and make attribution difficult, giving their campaigns more stealth and persistence.
There are several frameworks that have attracted the interest of bad actors other than Sliver. Campaigns run in recent months by a group thought to be supported by the Russian government have used Brute Ratel, a legal adversarial attack simulation program.
Sliver command-and-control framework and numerous other C2 frameworks are illustrations of how threat actors consistently try to avoid automated security detections, according to Microsoft.
In the report, Microsoft gave details of some examples of how Defender Experts search for these TTPs in customer environments to find Sliver and other new C2 frameworks.
The infrastructure of Sliver command-and-control framework
Like many C2 frameworks, Sliver supports a number of different network protocols, including DNS, HTTP/TLS, MTLS, and TCP. In order to pass as a good web server, it can also accept implant or operator connections and host files.
Starting listeners and checking them for anomalies is the first step in testing any C2 framework. Unique HTTP header combinations and JARM hashes, which are active fingerprinting methods for TLS servers, are two examples of common artifacts. Such a method for detecting Sliver and Bumblebees has been shared by RiskIQ.
Payloads
Sliver was created using the Go programming language (GoLang), therefore its implants work on all platforms. Operators can generate implants by default in a number of forms, including:
Executable, Shared Library/DLL, Shellcode, and Service
Stagers, which are smaller payloads with limited built-in features and are primarily designed to recover and launch a full implant, are also supported by Sliver. Many C2 frameworks include stagers to reduce the amount of harmful code in an initial payload (for example, in a phishing email). File-based detection may become more difficult as a result.
Operators don’t have to make use of Sliver’s standard DLL or executable payloads, though. Threat actors with the right motivation can create Sliver shellcode and include it into unique loaders like Bumblebee, which then executes the Sliver implant on a compromised system. If the shellcode isn’t encrypted, detection engineers can develop rules for the shellcode payload that is contained in the loader.
Config Settings extraction
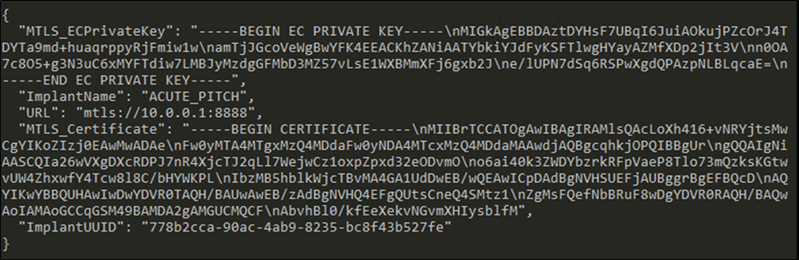
Security analysts may encounter a malware payload with limited context when responding to a suspected attack. The first step in looking for afflicted devices in the network is to quickly extract important configuration information from the virus, such as the C2 address, network configurations, and other implant characteristics.
To stall analysis and detection efforts, many implants, like Sliver, severely obscure or encrypt important information. Sliver, like other GoLang-based implants, accomplishes this using the public gobfuscate library. Although many researchers have developed methods to aid in “de-gobfuscating” strings in payloads, the procedure is still largely manual.
In these circumstances, loading configurations into memory makes it easier for us to extract the configurations we are interested in. To use its configurations, Sliver must first de-obfuscate and decrypt them, so we may scan memory for these values and programmatically extract them to obtain results like configuration data, as shown below:
Execution of code
Sliver comes with a number of built-in methods and post-exploitation features. Process injection, which is a mechanism for executing arbitrary code inside the address space of a different live process, is one of the most prevalent underlying techniques utilized by C2 operators and frameworks, Microsoft has stated.
Process injection is used by attackers for a variety of purposes, including defense evasion, access or privilege escalation, avoiding dangerous code execution, and more.
Process injection enables attackers to execute malicious code that poses as legitimate programs. Attackers can bypass easily recognizable custom processes by using code injection. Instead, they add malicious code to widely used, reliable programs (like as explorer.exe, regsvr32.exe, svchost.exe, etc.), which increases the stealth and persistence of their operations.
Microsoft researchers
Utilizing threat hunting to strengthen defenses against future threats
Our examination of Sliver’s functionality and source code offers hunting opportunities that can be applied to other malware frameworks. Furthermore, Sliver and numerous other C2 frameworks provide another illustration of the ongoing efforts made by threat actors to escape automated security detections. Threat hunting adds a layer of protection to existing security mitigations and can help with defense evasion issues. The detections and threat hunting procedures are more resistant to changes in attacker toolkits using those techniques in the future by concentrating research efforts on the fundamental attacker techniques employed within Sliver.
to Rewrite
Any of the titles in the security center, according to Microsoft, can reveal threat activity on a network, hence you’re expected to check if:
- A suspicious file has been dropped
- Group of rising threat behavior tied to ransomware discovered
- An ominous series of exploratory tasks
- An observation of suspicious behavior by cmd.exe
- A data transfer that is suspicious
- Process hollowing detected
- Discovery of suspicious System Network Configuration
- Discovery of suspicious peripheral device
- Potentially malicious code process injection
- Suspicious command launched from a remote location
- Abnormal Remote Service Execution
- Suspicious files or content obfuscation/de-obfuscation activity
The following security measures can also be used by Microsoft customers to lessen the effects of Sliver and other comparable threats:
- Activate network defense. Users that utilize network protection can avoid visiting risky IP addresses and domains. To prevent servers from connecting arbitrarily to the internet to browse or download data, check your perimeter firewall and proxy. Such limitations aid in preventing the download of malware and C2 activity, including on mobile devices.
- Use Microsoft Defender Firewall, which, in conjunction with your network firewall, tries to stop service message block (SMB) and remote procedure call (RPC) traffic along endpoints. The ability to attack laterally and in other ways is so restricted.
- Activate Microsoft Defender Antivirus’s cloud-delivered protection and automatic sample submission. With the use of artificial intelligence and machine learning, these capabilities can instantly recognize and neutralize brand-new threats.
- To verify you are blocking spoof emails, spam, and emails with viruses, check your Office 365 email filtering settings. For improved phishing defense and coverage against fresh threats and polymorphic variations, use Microsoft Defender for Office 365. Office 365 can be set up to erase sent mail and review links when they are clicked in response to fresh danger intelligence.
Organizations can also follow these general best practices to make their networks resilient against attacks:
- Harden the cloud
- Close security blind spots
- Reduce the attack surface
- Evaluate the perimeter
- Harden internet-facing assets


